Honeypot & Man In the Middle (MITM) Attacks on Wireless Networks
What is a Wireless Honeypot Attack?
Normally, when a wireless client (PC, Laptop) is switched on, it will try to probe the nearby area for access points for a particular SSID (SSID is like a name for the network, which is advertised in order for users and clients to associate with the access points). In this scenario, if a hacker is nearby (perhaps in the car parking), he could use access points with high power (gain) antennas with the same SSID as the corporate network SSID and respond to such client probe requests with a valid probe response. As the wireless clients generally associate with an access point with the highest power (signal strength), it can get associated to the access point belonging to the hacker.
Once the honeypot association is made by the attacker with a valid client from an internal corporate network, he can find out a lot of information about both the client and the network and use them to launch further attacks like Man In the Middle attack, Wireless Denial Of Service (DOS) attack, etc. So, as you can see, wireless honeypot itself is not an attack but it paves the way for other attacks.
Using Wireless Honeypot to detect Hacker Activities:
This is an interesting application of wireless honeypots and can be used by the administrators to detect and divert wireless hacker activities. In this method, a low cost access point/ soft-access point without any authentication/ encryption is deployed on a separate network (other than the corporate network) preferably with a few clients (PC’s) and some wireless traffic running between them. If any hacker is casually looking for open/ weak wireless access points to associate and attack, this honeypot will surely lure him in to it. That is the purpose of a honeypot!
Once a hacker connects to the wireless access point, all his activities could be monitored. Administrators could study the methods used by such hackers and see what information they are trying to capture/ which worms/ attacks they are trying to inject in to the network. By doing this, the motive and the methodology used by hackers can be studied. Moreover, a honeypot AP could (at least temporarily) keep the hacker engaged and alert the administrator so that the actual network can be safeguarded.
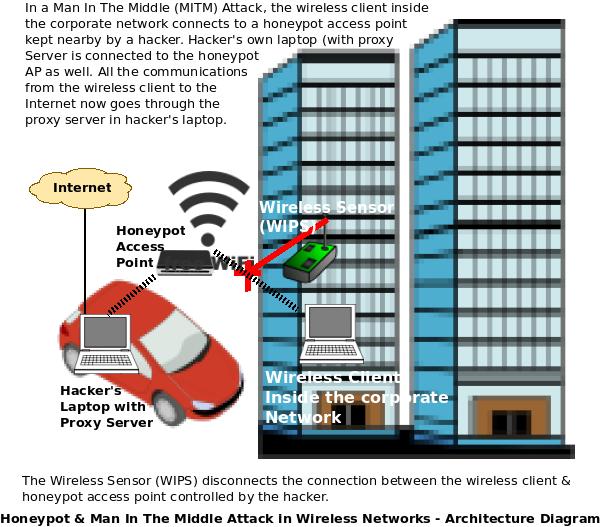
What is a Wireless Man In The Middle (MITM) Attack?
A Man In The Middle (MITM) attack is actually a continuation of the honeypot attack wherein a hacker would lure a wireless client to associate with his honeypot access point (either by increasing the honeypot access point’s signal strength using high gain antennas (or) by inducing a denial of service attack on the nearest legitimate AP with the highest signal strength) and utilizes his Laptop/ computer as a proxy server where all the communication between the wireless client (user) and the target host server goes through this proxy server. Initially, the target host server would be a public server placed on the Internet but if proper information is available, it could be an internal server as well.
So, obviously the attacker would hope that once a wireless client connects to his wireless network, the first thing it wants to do is to connect and browse over the Internet. Because, if the client wants to communicate with an internal server, the hacker cannot redirect the communication to the internal server as he cannot connect to it, yet. For the wireless client, Internet can always be connected through the hackers proxy server (installed in his Laptop) using a wireless data card (for instance).
This process is slightly more complicated. First, the wireless client sends a request to connect to a particular server in the Internet using a domain name. These domain names are resolved in to IP addresses using DNS lookup tables. At this moment, the hackers laptop (which is also connected to the same honeypot access point, sends a fake IP address (and perhaps even a fake certificate) , which is essentially same as the IP address of the hacker. When the client sends more requests, these are accepted by the proxy server installed in the clients laptop and forwarded over the Internet to the real public servers. When the proxy server gets the response from the Internet, the same is again transferred back to the wireless client which had requested it originally.
So, the wireless client thinks that the responses are coming from the public server directly, but the responses are actually forwarded through the proxy server of the hacker. Now, since all the information flows through the proxy server in his laptop, the hacker can get a lot of information including web-mail user-name/passwords etc.
How to detect a Honeypot/ Man In The Middle (MITM} Attack on the wireless network?
One of the ways in which a Wireless Intrusion Prevention System detects a Honeypot/ Man In The Middle (MITM) attack is by recording the BSSID (MAC address of access points), ESSID (Wireless Network Name), Channel and Signal Strength information for all the access points in the wireless network.
If any combination of those parameters do not match for an access point, then there is a chance that this AP is a Honeypot AP. The channel information is important because, even if the honeypot AP uses the same ESSID and BSSID information, the channel would most probably be different (Especially if the legitimate AP is taken down using a Denial Of Service attack as the honeypot AP needs to operate away from that channel).
But there is a chance that the hacker makes the honeypot AP operate in the same SSID/channel as the legitimate AP. In these cases, the signal strength information is compared in addition to all the other parameters. A honeypot AP will have totally different levels of signal strength when compared to the legitimate AP. So, this information can also be used.
Some Wireless Intrusion Prevention Systems check if the access point is present in both wired as well as wireless networks. A honeypot is generally placed outside the wired network, and hence this factor helps in identifying them. For stopping this attack, the wireless connection between the honeypot access point and the wireless client could be disconnected by using disconnection frames (reverse DOS attack).
excITingIP.com
You can stay up to date with the various computer networking technologies by subscribing to this blog using your email address in the box written as “Get Email updates when new articles are published”